Thursday, 30 April 2015
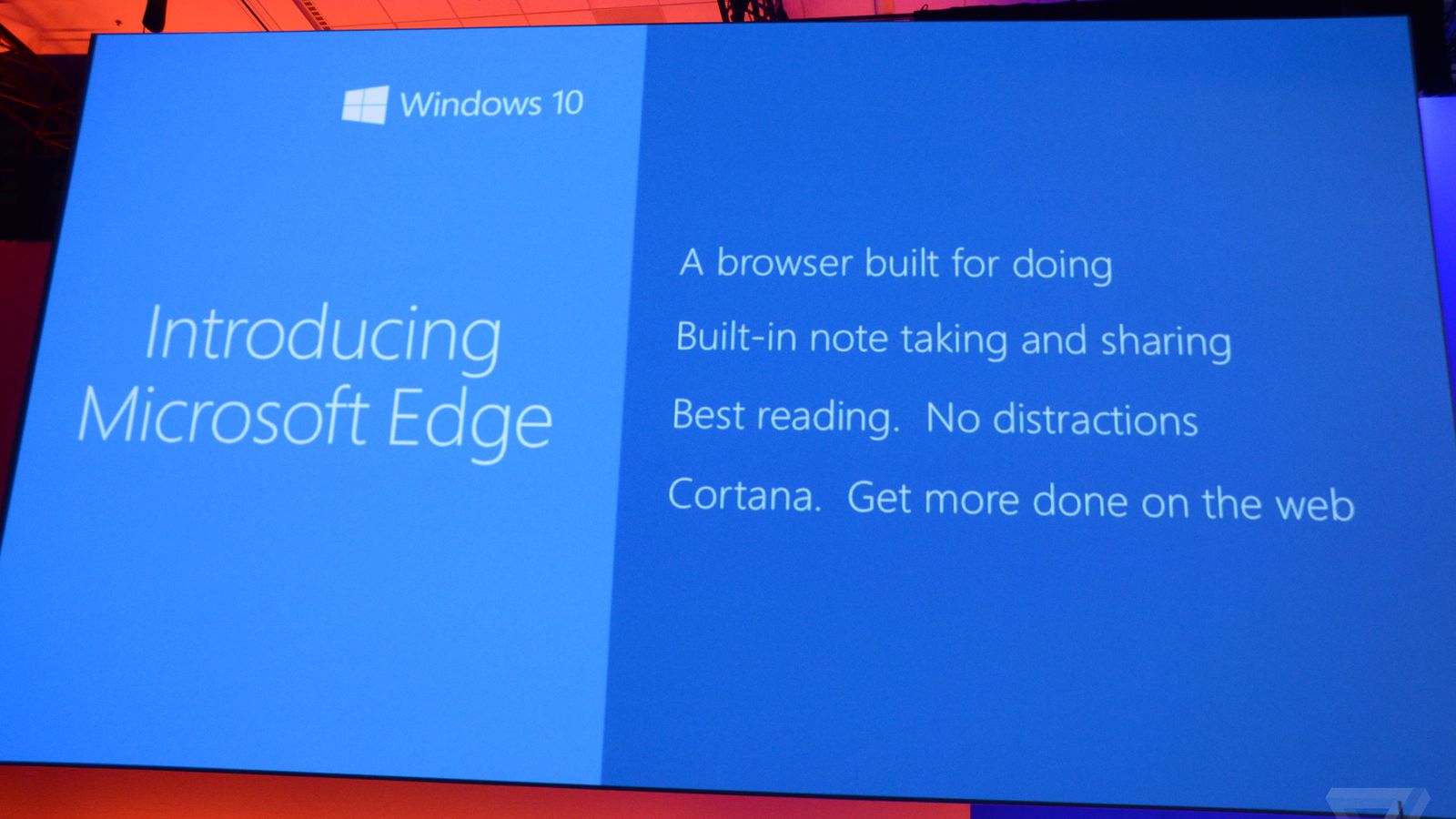
Microsoft: Microsoft's New Browser: Microsoft 'Edge'
Microsoft announced the oficial name of its new browser during the opening day of its Build 2015 show.
The final name is not "Spartan," which was the codename for the browser, as many had hoped and predicted. Instead, it's Microsoft "Edge."
"It's the browser built for getting things done," is the new marketing slogan.
Even though Microsoft officials have been adamant in insisting that Spartan is not Internet Explorer -- and, in fact, is such a different fork of that browser that it's something totally new -- the new name is still fairly close to IE.
There's actually a good reason for that, in my opinion."Normal" users are very familiar with the current IE logo -- the stylized lowercase "e." They know if they click on the "e," they open a Web browser. If Microsoft suddenly changed that logo to an "s" or another new image/letter, there might be confusion among at least some of its user base.
Edge will be the only browser supported on Windows 10 Mobile devices. Microsoft will make both IE and Edge available on devices running Windows 10 Desktop on PCs, desktops, laptops and larger tablets, for backwards-compatibility reasons. Edge is integrated with Cortana and will be a Universal app, meaning it will be available for download, and be updated, from the Store.
If you're wondering about the significance of "Edge," it's the name of the rendering engine inside Microsoft's new browser.
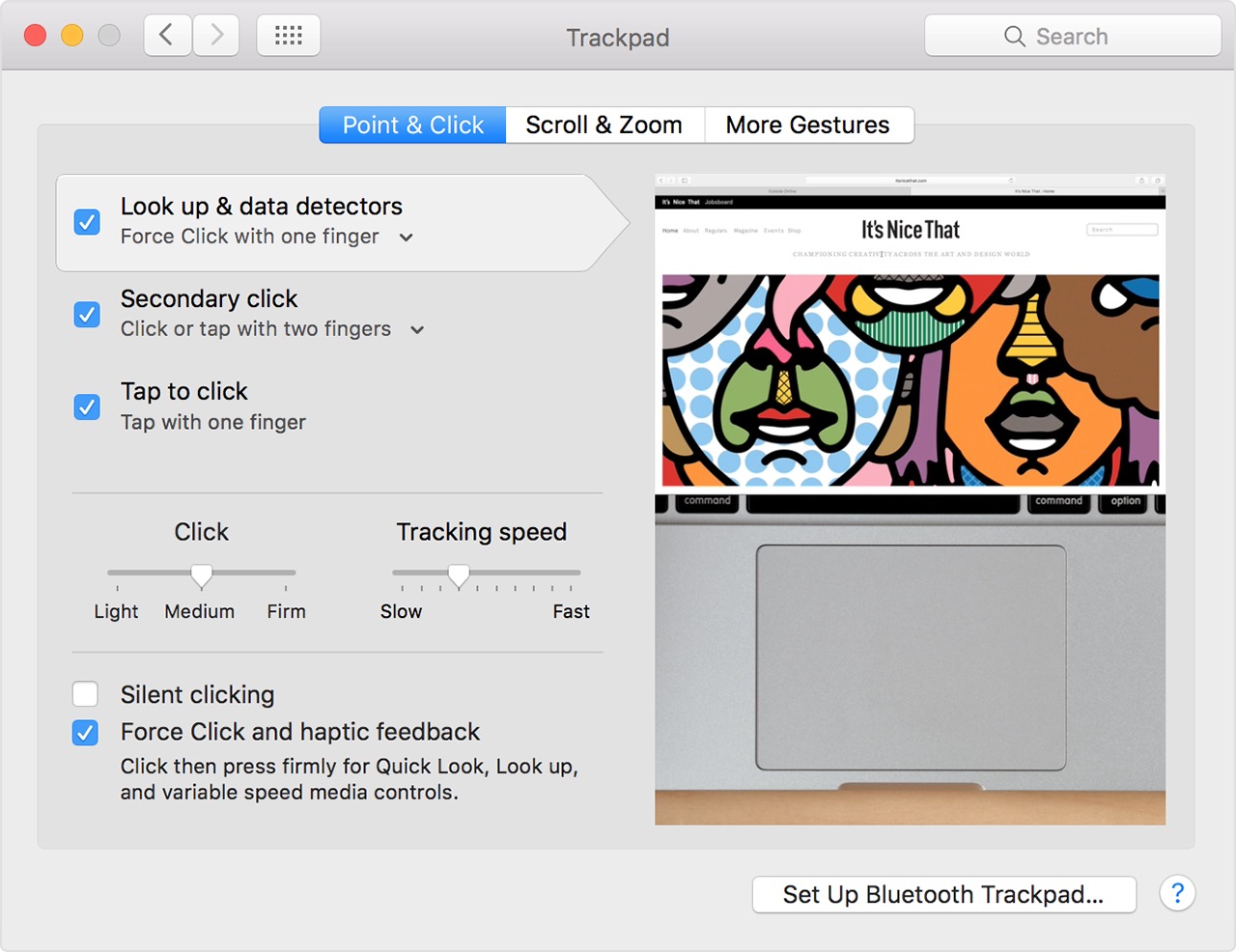
Apple: Force Touch Trackpad
The Force Touch trackpad lets you Force click. You Force click by pressing on the trackpad and then applying more pressure. This allows you to take advantage of new functionality in many apps and system features on your Mac.
To see a video of a Force click, select the Apple menu and choose System Preferences. Then choose Trackpad, click the “Point & Click” tab, and hover the pointer over the “Look up & data detectors” checkbox.
Here are some examples what you can do with a Force click.
> Look up: Force click text in a webpage or Mail message and a popover appears showing you Look up results for that text. Information appears from sources like Dictionary, Wikipedia, and more.
> Addresses: Force click an address to see a Maps preview of that location.
> Events: Force click dates and events to add them to Calendar.
> Link previews: Force click a link in Safari or Mail to see an inline preview of the webpage.
> Tracking numbers: Force click a tracking number in Safari or Mail to see shipping details in a popover.
> File icons: Force click a file icon to see a Quick Look preview of the file's content.
> File names: Force click a file name in the Finder or on your desktop to let you edit the file name.
> Dock: Force click an app icon in the Dock to access App Exposé. This shows you all of your open windows for that app.
> Mail: When composing a message with an image or PDF attachment in it, Force click the attachment to activate Markup. This lets you annotate the attachment.
> Messages: Force click a conversation in the sidebar to see details and attachments. Force click a buddy’s token in the chat header to see their contact card in a popover.
> Reminders: Force click a reminder to see more details.
> Calendar: Force click an existing event to see more details. Force click a meeting attendee to see their contact card in a popover.
> Map locations: Force click a location in a map to drop a pin there.
> iMovie: When your iMovie project has an animated Map or Globe, you can Force click the map in the Timeline to access a Style menu. This lets you choose different styles.
> QuickTime and iMovie: You can vary the pressure you use on fast-forward and rewind buttons. This will accelerate the speed at which you fast forward or rewind.
> iMovie: When dragging a video clip to its maximum length, you’ll get feedback letting you know you’ve hit the end of the clip. Add a title and you’ll get feedback as the title snaps into position at the beginning or end of a clip. Subtle feedback is also provided with the alignment guides that appear in the Viewer when cropping clips.
> Map zooming: Press harder on a zoom button to accelerate as you zoom in and out of a map.
> Photo arrowing: When you arrow through Photos in an Album or a Moment, you can apply additional pressure to go faster.
> Rotate photos: In Photos, when you choose Crop and then rotate a photo, and you’ll feel a notch when the rotation of the photo is at zero degrees.
To adjust the pressure you need to click your trackpad, follow these steps.
1. From the Apple menu, choose System Preferences.
2. Click Trackpad.
3. Click the "Point & Click" tab.
4. Find "Click pressure" and adjust the slider to your preference. Note that the sound of the click changes with the click pressure setting.
To turn off Force click, deselect the “Force Click and haptic feedback” checkbox. This will disable the functionality described in the Trackpad preferences pane.
A few of the examples of what you can do with a Force click only work if "Force click with one finger" is active. You enable or disable this in the "Point & Click" tab under "Look up & data detectors."
When you press the power key, your trackpad and keyboard become active after the startup tone. Your trackpad needs power to provide "haptic feedback" like clicking. When you turn your computer off, you turn off the trackpad too.
Apple: Adobe PDF Plug-in in Safari
<< Configuring Acrobat to display PDF files in Safari >>
The AdobePDFViewer plug-in is used to display PDF files in Safari using Acrobat and Reader. This plug-in is installed as part of the Acrobat X or Reader X installation. The location of this plug-in is:
/Library/Internet Plug-ins/AdobePDFViewer.plugin
<< Troubleshoot Known Issues >>
Reader's Preferences > Internet > Display PDF in Browser is always dimmed
* To disable Safari integration, delete the AdobePDFViewer.plugin from /Library/Internet Plug-ins
* To reenable Safari integration, rerun the installer over the current installation. Start the Acrobat/Reader X installer from the original media, and then follow the onscreen prompts to complete the installation.
Uninstalling an older version of Acrobat or Reader after Acrobat X or Reader X has been installed removes the AdobePDFViewer plug-in
If Acrobat X or Reader X is installed alongside an older version of Acrobat or Reader, removing the older version removes the AdobePDFViewer plug-in.
To reenable Safari integration, rerun the installer over the current installation. Start the Acrobat/Reader X installer from the original media, and then follow the onscreen prompts to complete the installation.
Older versions of the AdobePDFViewer plugin can overwrite newer versions of the plug-in
Having multiple versions of Acrobat or Reader installed on the same system can cause plug-in conflicts. For example, suppose you have both Acrobat 9 and Acrobat X on your system and Acrobat 9 gets updated. In this case, the Acrobat 9 version of the AdobePDFViewer plug-in can overwrite the Acrobat X version of the plug-in. To correct the issue, follow these steps:
1. Remove the previous version of Acrobat or Reader.
2. Reinstall Acrobat X or Reader X from the original media.
The AdobePDFViewer plug-in is used to display PDF files in Safari using Acrobat and Reader. This plug-in is installed as part of the Acrobat X or Reader X installation. The location of this plug-in is:
/Library/Internet Plug-ins/AdobePDFViewer.plugin
<< Troubleshoot Known Issues >>
Reader's Preferences > Internet > Display PDF in Browser is always dimmed
* To disable Safari integration, delete the AdobePDFViewer.plugin from /Library/Internet Plug-ins
* To reenable Safari integration, rerun the installer over the current installation. Start the Acrobat/Reader X installer from the original media, and then follow the onscreen prompts to complete the installation.
Uninstalling an older version of Acrobat or Reader after Acrobat X or Reader X has been installed removes the AdobePDFViewer plug-in
If Acrobat X or Reader X is installed alongside an older version of Acrobat or Reader, removing the older version removes the AdobePDFViewer plug-in.
To reenable Safari integration, rerun the installer over the current installation. Start the Acrobat/Reader X installer from the original media, and then follow the onscreen prompts to complete the installation.
Older versions of the AdobePDFViewer plugin can overwrite newer versions of the plug-in
Having multiple versions of Acrobat or Reader installed on the same system can cause plug-in conflicts. For example, suppose you have both Acrobat 9 and Acrobat X on your system and Acrobat 9 gets updated. In this case, the Acrobat 9 version of the AdobePDFViewer plug-in can overwrite the Acrobat X version of the plug-in. To correct the issue, follow these steps:
1. Remove the previous version of Acrobat or Reader.
2. Reinstall Acrobat X or Reader X from the original media.
Google: Adobe PDF Plug-in in Google Chrome
By default, Chrome uses a built-in PDF viewer to open PDFs. If you've disabled the built-in PDF viewer, Chrome will use Adobe Acrobat or Adobe Reader to display PDFs. You can also choose to make Adobe Acrobat or Adobe Reader your default PDF viewer in Chrome. Here's how:
1. Enter chrome://plugins into your address bar.
2. Scroll down to either Adobe Acrobat or Adobe Reader. (You'll only see them if you have them installed.)
3. Click the Enable link.
1. Enter chrome://plugins into your address bar.
2. Scroll down to either Adobe Acrobat or Adobe Reader. (You'll only see them if you have them installed.)
3. Click the Enable link.
Wednesday, 29 April 2015
Apple: Replace The Superdrive on Your MacBook Pro with A Secondary Hard Disk
You may replace the Superdrive on your MacBook Pro with a secondaty hard disk as follows:
Video - https://www.youtube.com/watch?v=YWUKAUlxrkg
Webpage - http://www.macworld.com/article/2082572/advice-from-an-apple-tech-how-to-replace-the-optical-drive-in-a-unibody-macbook-pro-with-a-second-h.html
OptiBay - http://store.mcetech.com/Merchant2/merchant.mvc?Screen=PROD&Product_Code=OBSXGB-UNB&Category_Code=STORHDOPTIBAY&Product_Count=0
IT Technology: No More Jaring in Malaysia?
Malaysia's first internet provider Jaring Communications Sdn Bhd has been put under the care of a liquidator after a court order last Thursday.
The news was met with a mix of sadness and happiness by a key figure who was instrumental in pioneering the internet service in the country some 30 years ago, Dr Mohamed Awang Lah.
In a Facebook posting, the former Jaring Chief Executive Officer said he was sad that the entity he had helped to start back in 1986 under the name RangKoM, later launched as Jaring in 1992, had been left to deteriorate into the present condition.
Jaring was also a subsidiary of Mimos and subsequently taken over by the Finance Ministry in 2007. "I no longer have any links with this company after retiring in 2010. However, to me this incident is to me sad and happy at the same time.
"Sad because the entity that introduced internet service in Malaysia has come to this. Happy because a more responsible party has been given the duty to manage it temporarily.
"I hope it will be turned around soon," he said.
After retiring, Mohamed's position was taken over by Nik Abdul Aziz Nik Yaacob as the new appointed CEO on March 1, 2011.
In August last year, Jaring was reportedly bought over by Utusan Printcorp for over RM100 million.
A few months later in October, The Malaysian Insider reported some 70 Utusan Printcorp staff held a protest to demand their unpaid salaries which was three months in arrears. Jaring staff were also among those reported not to have received their pay.
Jaring was also among three contractors that received a full payment of RM88.13 million by the Ministry of Communication and Multimedia for an incomplete broadband project in Sabah and Sarawak, according to the first series of the Auditor-General's Report 2014.
During his time as Jaring CEO, Mohamed was known as a proponent of an open access system for the broadband network. The Edge reported in 2008, that his stance was for the ownership of the network to be independent of the service provider.
Mohamed was also senior vice-president of Mimos Berhad and had been responsible for managing Jaring and supervising research and development operations in Mimos.
He started his career as an engineer at the National Electricity Board in 1976 and was also a tutor for the faculty of engineering in Universiti Malaya and the faculty deputy dean since 1983.
He obtained a first class honours degree in electronics and electrical engineering from King's College, University of London, in 1976 and has a PhD in Electronics and Electrical Engineering from the same university in 1980.
The news was met with a mix of sadness and happiness by a key figure who was instrumental in pioneering the internet service in the country some 30 years ago, Dr Mohamed Awang Lah.
In a Facebook posting, the former Jaring Chief Executive Officer said he was sad that the entity he had helped to start back in 1986 under the name RangKoM, later launched as Jaring in 1992, had been left to deteriorate into the present condition.
Jaring was also a subsidiary of Mimos and subsequently taken over by the Finance Ministry in 2007. "I no longer have any links with this company after retiring in 2010. However, to me this incident is to me sad and happy at the same time.
"Sad because the entity that introduced internet service in Malaysia has come to this. Happy because a more responsible party has been given the duty to manage it temporarily.
"I hope it will be turned around soon," he said.
After retiring, Mohamed's position was taken over by Nik Abdul Aziz Nik Yaacob as the new appointed CEO on March 1, 2011.
In August last year, Jaring was reportedly bought over by Utusan Printcorp for over RM100 million.
A few months later in October, The Malaysian Insider reported some 70 Utusan Printcorp staff held a protest to demand their unpaid salaries which was three months in arrears. Jaring staff were also among those reported not to have received their pay.
Jaring was also among three contractors that received a full payment of RM88.13 million by the Ministry of Communication and Multimedia for an incomplete broadband project in Sabah and Sarawak, according to the first series of the Auditor-General's Report 2014.
During his time as Jaring CEO, Mohamed was known as a proponent of an open access system for the broadband network. The Edge reported in 2008, that his stance was for the ownership of the network to be independent of the service provider.
Mohamed was also senior vice-president of Mimos Berhad and had been responsible for managing Jaring and supervising research and development operations in Mimos.
He started his career as an engineer at the National Electricity Board in 1976 and was also a tutor for the faculty of engineering in Universiti Malaya and the faculty deputy dean since 1983.
He obtained a first class honours degree in electronics and electrical engineering from King's College, University of London, in 1976 and has a PhD in Electronics and Electrical Engineering from the same university in 1980.
IT Technology: Prey
Prey is a application that allow you to keep track of your laptop, phone and tablet whenever missing, whether you're in town or abroad. Open source, proven software with hundreds of documented recoveries all around the world.
What can Prey do?
1. Protect what you paid for
Not only do we depend on our mobiles and laptops on a daily basis: they also cost money. If getting robbed is painful, paying twice for something you already bought is even worse.
2. One place to find them all
Prey works on all major operating systems, so it lets you keep track and trigger actions on all your devices from a single place. Like a universal remote control, but for gadgets.
3. Prevent unauthorized access
When your data is at stake, bad things can happen. Use Prey to fully lock down your devices and delete your stored passwords, to ensure that no one will have access to your private stuff.
4. Because privacy comes first
Sensitive data is gathered only when you request it, and is for your eyes only -- nothing is sent without your permission. You can always check our source code if you want to make sure.
Friday, 24 April 2015
Apple: How to Move an iPhoto Library into Photos for Mac
Mac users coming from iPhoto may wish to move an iPhoto Library to the new Photos app. While importing is an option when first setting up the Photos app in OS X, many users many have skipped the initial setup screens and missed that opportunity to import pictures and images into Photos from apps like Aperture and iPhoto. Fortunately, it’s very easy to add an iPhoto library into the Mac Photos app at any time.
Much like making an entirely new Photos library in OS X, you’ll need to use the Option key during application launch to be able to migrate an iPhoto library into Photos app.
<< Moving an iPhoto Library into Photos App of OS X >>
1. Quit out of Photos app (and iPhoto) if you haven’t done so already
2. Relaunch the Photos app and immediately hold down the Option key until you see the Library selection screen, then choose one of the following options:
> If you see the iPhoto library in the list, simply select it and choose “Choose Library” to open it within Photos app
> Otherwise, select “Other Library” and navigate to the location of the iPhoto library you wish to import into Photos app, then open it as usual
3. Let Photos app import the iPhoto library, it should happen almost immediately but very large libraries or those stored on slower external volumes may take some time
If you already have a busy Photos library, you’re going to be working with two different image libraries now, which is why it’s generally best to allow Photos app to pull in your iPhoto or Aperture library on first launch.
If you’d like to merge two different libraries, well, at the moment, there is no way to directly perform a merging of an iPhoto library with a Photos library without manually intervening and importing photos on your own. You can do that through the File > Import menu item, or by dragging and dropping images from one library into another using the file system. Being able to directly merge libraries together would be pretty useful, so it’s possible that such a feature could be introduced into future versions of Photos for OS X. In the meantime, you can always create new libraries and use separate libraries by switching between them by using the Option key on Photos app launch.
Tuesday, 21 April 2015
Apple: AdwareMedic - Adware Removal Tool
AdwareMedic removes all known adware from your Mac. It is very simple to use, and should clean up your system in less than a minute, from start to finish. Just open the app, click the Scan for Adware button, and remove anything that is detected. That's it!
If AdwareMedic doesn’t solve your problem, it includes the ability to take a system snapshot that can help find possible sources for the problem. This both helps you get rid of the adware and helps others by improving the app!
AdwareMedic will not install anything on your system. When it is opened, it will connect to adwaremedic.com to check for and/or download the latest adware "signatures" (a small text file that tells AdwareMedic how to identify adware components).
AdwareMedic requires a Mac running Mac OS X 10.7 (Lion) or later.
Although AdwareMedic functions somewhat like anti-virus software, it’s important to understand that it is not anti-virus software! It does not remove any real malware – only adware. If you think you may be infected with actual malware, be aware that there is nothing that can reliably remove all malware.
It is also important to understand that AdwareMedic does not protect you against adware. AdwareMedic simply removes adware. Using AdwareMedic will not prevent you from being "infected" with adware again in the future. For that matter, neither will using anti-virus software; only a change in your online habits can keep you safe.
>> What is adware?
Adware is unwanted software that uses sneaky and dishonest methods to get installed on your computer, and then changes the behavior of your web browser. Once installed, it does things like injecting advertisements into web pages, causing pop-up windows or tabs to open to advertising sites, and changing your home page and/or search engine.
Although adware sounds like malware, there is a crucial difference: adware on the Mac has never been documented to involve keylogging, back doors or any other such malicious activities... just unwanted advertising. As such, most anti-virus software doesn't bother to detect most adware, and if it does, it doesn't do a very comprehensive job of detecting it. This is where AdwareMedic comes in - it detects the adware that anti-virus software doesn't.
>> Where did it come from?
The short answer: from an installer for some app you were tricked into downloading from an unsavory site. This may be a site like Download.com or Softonic, or a site offering streaming of "free" videos, or from a piracy site or torrent, or something else similar.
If AdwareMedic doesn’t solve your problem, it includes the ability to take a system snapshot that can help find possible sources for the problem. This both helps you get rid of the adware and helps others by improving the app!
AdwareMedic will not install anything on your system. When it is opened, it will connect to adwaremedic.com to check for and/or download the latest adware "signatures" (a small text file that tells AdwareMedic how to identify adware components).
AdwareMedic requires a Mac running Mac OS X 10.7 (Lion) or later.
Although AdwareMedic functions somewhat like anti-virus software, it’s important to understand that it is not anti-virus software! It does not remove any real malware – only adware. If you think you may be infected with actual malware, be aware that there is nothing that can reliably remove all malware.
It is also important to understand that AdwareMedic does not protect you against adware. AdwareMedic simply removes adware. Using AdwareMedic will not prevent you from being "infected" with adware again in the future. For that matter, neither will using anti-virus software; only a change in your online habits can keep you safe.
>> What is adware?
Adware is unwanted software that uses sneaky and dishonest methods to get installed on your computer, and then changes the behavior of your web browser. Once installed, it does things like injecting advertisements into web pages, causing pop-up windows or tabs to open to advertising sites, and changing your home page and/or search engine.
Although adware sounds like malware, there is a crucial difference: adware on the Mac has never been documented to involve keylogging, back doors or any other such malicious activities... just unwanted advertising. As such, most anti-virus software doesn't bother to detect most adware, and if it does, it doesn't do a very comprehensive job of detecting it. This is where AdwareMedic comes in - it detects the adware that anti-virus software doesn't.
>> Where did it come from?
The short answer: from an installer for some app you were tricked into downloading from an unsavory site. This may be a site like Download.com or Softonic, or a site offering streaming of "free" videos, or from a piracy site or torrent, or something else similar.
Google: Find My Phone
Here’s a helpful tip for Android smartphone users who can’t quite keep track of their devices on the day-to-day: you can always search for your missing Android device on Google.
All you have to do is type “Find my phone” into Google Search, and you’ll be sent into the Android Device Manager on your browser. The search engine will then locate your phone on a Google map. It even tells you the make and model of your device. It even found my exact address. The Device Manager guarantees the search is accurate up to 24 meters.
From the Device Manager, you have the option to ring your device. You know, for all those annoying times you’ve left your phone in the laundry basket or in the bathroom or its fallen under your bed. Whatever the case, this handy Google app will help you find the device.
What if your device has been stolen? Sure, you can locate it on the map, but if it’s on the other side of the country, it won’t help you much. That’s why you also have the option to lock your phone and/or erase everything on the device.
All you have to do is type “Find my phone” into Google Search, and you’ll be sent into the Android Device Manager on your browser. The search engine will then locate your phone on a Google map. It even tells you the make and model of your device. It even found my exact address. The Device Manager guarantees the search is accurate up to 24 meters.
From the Device Manager, you have the option to ring your device. You know, for all those annoying times you’ve left your phone in the laundry basket or in the bathroom or its fallen under your bed. Whatever the case, this handy Google app will help you find the device.
What if your device has been stolen? Sure, you can locate it on the map, but if it’s on the other side of the country, it won’t help you much. That’s why you also have the option to lock your phone and/or erase everything on the device.
IT Technology: What Do You Think About Transparent Caches?
Transparent caches observe HTTP traffic passing through the network, storing a copy of downloaded content. Then the next time a user requests that object, it can be served from the local cache, instead of from the remote server. This can save significant amounts of upstream bandwidth, as popular objects only need to be requested once. It can also improve the user experience, by delivering frequently accessed content faster. This is particularly noticeable for low-bandwidth, high-latency links.
Traffic is redirected to Transparent Caches using techniques such as Policy-Based Routing, WCCP, or inline deployment, where all traffic goes through the cache. No end-user configuration is required (that’s the ‘transparent’ part!).
>> The Problems with Transparent Caches
I’ve evaluated some transparent caches recently, and they have a number of issues:
1. Cost: They are very expensive to deploy, and they don’t have a viable payback time for money saved in bandwidth costs – and that’s without even factoring in falling bandwidth costs.
2. Performance: Systems like the Blue Coat CacheFlow top out at around 2Gbps of throughput. That sounded OK a few years ago, but now is looking fairly lame for a hardware appliance. Surely I could get more out of a Virtual Appliance?
3. Poor Deployment Options: Blue Coat has the cheek to say they have: “…tight integration with existing infrastructure. This includes integration with routers from Cisco and Juniper…” – but when you look into it, their only option is using Policy-Based Routing! Want more than one? You’ll need to buy a separate load-balancer for that. Other vendors offer WCCP, but I’ve heard that charitably described as “the best broken chair in the dump“. Asymmetric traffic is a problem, similar to having stateful firewalls in your network.
4. Changing nature of content: There’s a growing shift towards SSL, and most of us can’t read that. No visibility means no caching. Object size is a problem too – sure we can transparently cache lots of funny cat videos, but how do we do that in a workable manner for multiple sources of movie-size video files?
5. Lack of Content Integration: Transparent cache providers may claim they are “intelligent” because they look at real traffic patterns, and detect what should be cached. The problem is that they have to make assumptions about that content, and they sometimes get it wrong, and serve up out of date content. Transparent cache operators will be aware of the need to apply “bypass” rules for specific sites.
>> CDNs – Our Only Realistic Option Right Now
Rather than using generic caches, we can use caches provided by Content Delivery Networks (CDNs). These systems host large amounts of content, from one or more content providers. These aren’t transparent – through DNS tricks, users are redirected to the content hosted on the CDN edge node closest to the end user. They may not host all content – they can act as a proxy, automatically retrieving content.
CDN Operators such as Akamai charge content providers for using their services. Google also has caching systems – particularly useful for YouTube. Netflix also offers CDN edge nodes to any ISP that wants to host them. The CDN operators don’t charge the service provider for these systems – they charge the content providers instead.
ISPs traffic profiles usually show that a few sources – YouTube, Netflix, etc. dominate their overall traffic patterns. If a couple of sources could be delivered from a CDN instead, there’s not much cost advantage in transparent caching the rest of the data.
Because the CDN operator manages the content on their systems, and they manage how clients retrieve that content (through DNS, etc), then they are in full control of the delivery. They know that they’ve cached complete objects, and they can pre-populate content they know will be popular. SSL can still work too, since the CDN knows the content being delivered, and it can tell the client the URL to retrieve content from. No tricky manipulation of traffic flows either. From an ISP’s perspective, it’s like hosting a web server. No funny path manipulation, and no problems with asymmetric traffic. Typical performance numbers show 30% of traffic can be served up by the CDN caches.
>> No Future for Transparent Caches Then?
There are some specific situations where you might want to cache all traffic – e.g. if you’re a large New Zealand-based ISP that sells International transit to other ISPs. By transparently caching, you can charge your clients International bandwidth rates, even if some of the content was delivered from a local cache. With that business model, if they moved to hosting CDN nodes, it would only be Domestic traffic to clients, and that’s far cheaper. (Unless of course they put their CDN caches into their International VRF, but that would be sneaky, and surely they wouldn’t do that, right? Right?)
There is also a possible future where the Transparent caches could somehow have a standardised signalling with the content providers, marking content, and pre-delivering it to the caches. I presume that is what these working groups are talking about. But when you dig into it, it sounds an awful lot like a CDN. The advantage would be that you could host just one CDN/Cache within your network, instead of needing to host boxes from Akamai, Google, Netflix, etc. It sounds like it might have promise. But think about the vested interests here, and the difficulties of trying to get everyone to work together. Likely to happen? Not any time soon.
Google: Inbox by Gmail for Google Apps
Have you ever felt like your inbox was someone else’s to-do list? Requests, project updates and action items stream in all day. You move between your computer and the phone in your pocket to try to manage, and instead of focusing on the most important things, you find yourself focusing on the most recent things. No matter the device, email should feel like a time saver, but instead it feels like a chore.
This is why we created Inbox by Gmail, to help you focus on the things that matter to you. Since we launched five months ago, one of the biggest pieces of feedback we’ve received is that Google Apps customers want access to Inbox at work. That’s why we're excited to kick off the next phase of our journey: collaborating with you to bring Inbox to work.
Even before the first invitations went out to use Inbox for your own email, Googlers have been using it to get more done at work. Whether it’s snoozing the expense report notification until after the big presentation, or adding a reminder to schedule lunch with a favorite client, Inbox helps put email on your terms. And since Inbox was built on the same infrastructure as Gmail, it meets the same high security standards you expect from email.
Of course, every company and every person is different, so we want to get more input on how Inbox will work at your company. Starting next month, we’ll begin enabling Inbox for a small group of Google Apps customers to learn about their needs, challenges and use cases.
Inbox wasn’t created to reinvent email, Inbox was created to help you reinvent the way you get things done. This means we need to understand more about how things get done (or don’t) today. And with your feedback, who knows, we could reinvent the way people work.
This is why we created Inbox by Gmail, to help you focus on the things that matter to you. Since we launched five months ago, one of the biggest pieces of feedback we’ve received is that Google Apps customers want access to Inbox at work. That’s why we're excited to kick off the next phase of our journey: collaborating with you to bring Inbox to work.
Even before the first invitations went out to use Inbox for your own email, Googlers have been using it to get more done at work. Whether it’s snoozing the expense report notification until after the big presentation, or adding a reminder to schedule lunch with a favorite client, Inbox helps put email on your terms. And since Inbox was built on the same infrastructure as Gmail, it meets the same high security standards you expect from email.
Of course, every company and every person is different, so we want to get more input on how Inbox will work at your company. Starting next month, we’ll begin enabling Inbox for a small group of Google Apps customers to learn about their needs, challenges and use cases.
- Do you want to use Inbox as your primary email at work?
- Are employees at your company heavy mobile users?
- Most importantly, do you want to partner with Google on user studies to help build the new work Inbox?
Inbox wasn’t created to reinvent email, Inbox was created to help you reinvent the way you get things done. This means we need to understand more about how things get done (or don’t) today. And with your feedback, who knows, we could reinvent the way people work.
Monday, 20 April 2015
Microsoft: View Exchange Certificate Properties
The following steps allow you to view the Exchange certificate properties:
1. Open Exchange Management Console ( EMC ).
2. In the console tree, click Server Configuration.
3. Select the server that contains the certificate, and then select the certificate you want to view.
4. From the action pane, click Open.
==> You can view information about the certificate on the General, Details, and Certification Path pages of the Exchange Certificate dialog box.
1. Open Exchange Management Console ( EMC ).
2. In the console tree, click Server Configuration.
3. Select the server that contains the certificate, and then select the certificate you want to view.
4. From the action pane, click Open.
==> You can view information about the certificate on the General, Details, and Certification Path pages of the Exchange Certificate dialog box.
Friday, 17 April 2015
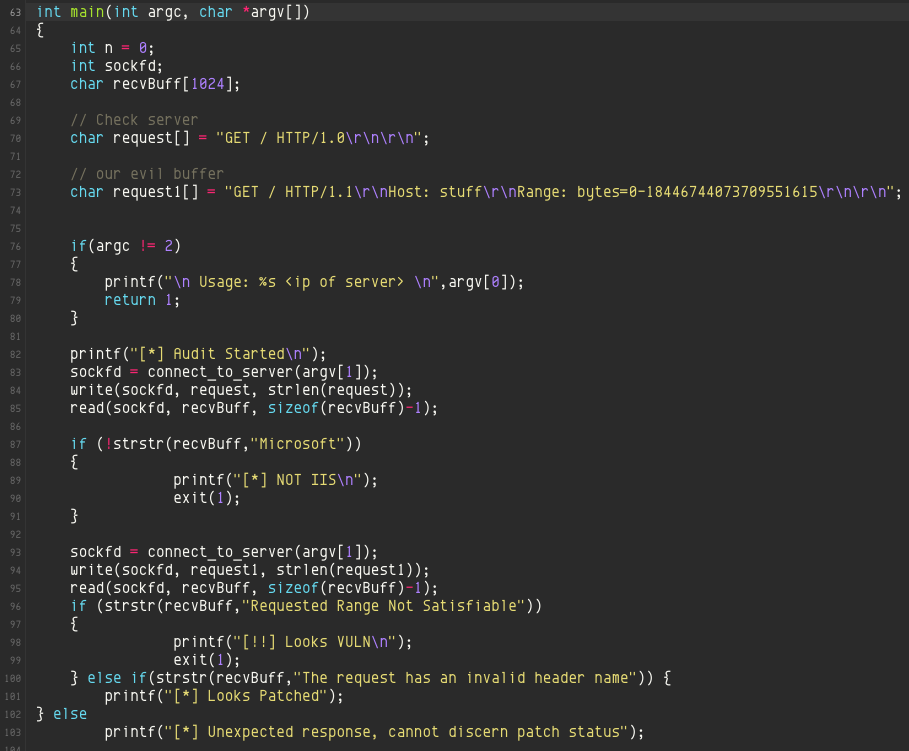
IT Security: HTTP.sys Remote Code Execution Vulnerability ( CVE-2015-1635 )
A remote code execution vulnerability exists in the HTTP protocol stack (HTTP.sys) that is caused when HTTP.sys improperly parses specially crafted HTTP requests. An attacker who successfully exploited this vulnerability could execute arbitrary code in the context of the System account. To exploit this vulnerability, an attacker would have to send a specially crafted HTTP request to the affected system.
Tuesday, 14 April 2015
Apple: Configure Startup Application in Mac OS X
There are two method to configure the startup application in Mac OS X:
Method 1:
Add the application to the user's "Login Items" (under System Preferences=>Accounts=[user])
Method 2:
Add a launchd agent to the user's ~/Library/LaunchAgents folder
You may create a new launch agent file as follows:
~/Library/LaunchAgents/my.everydaytasks.plist
With contents:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>Label</key>
<string>my.everydaytasks</string>
<key>ProgramArguments</key>
<array>
<string>/Applications/EverydayTasks.app/Contents/MacOS/EverydayTasks</string>
</array>
<key>ProcessType</key>
<string>Interactive</string>
<key>RunAtLoad</key>
<true/>
<key>KeepAlive</key>
<false/>
</dict>
</plist>
Method 1:
Add the application to the user's "Login Items" (under System Preferences=>Accounts=[user])
Method 2:
Add a launchd agent to the user's ~/Library/LaunchAgents folder
You may create a new launch agent file as follows:
~/Library/LaunchAgents/my.everydaytasks.plist
With contents:
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>Label</key>
<string>my.everydaytasks</string>
<key>ProgramArguments</key>
<array>
<string>/Applications/EverydayTasks.app/Contents/MacOS/EverydayTasks</string>
</array>
<key>ProcessType</key>
<string>Interactive</string>
<key>RunAtLoad</key>
<true/>
<key>KeepAlive</key>
<false/>
</dict>
</plist>
VMware: Independent Non-Persistent Mode Not Functioning
For non-persistent mode, the changes are discarded only if you power off the VM (or shutdown the VM). Rebooting VM or reseting VM is different from power OFF and shutdown.
Try to power OFF or shut down the VM for the non-persistent mode to take effect.
Try to power OFF or shut down the VM for the non-persistent mode to take effect.
Apple: Preference / PLIST Files Modification Issue
Something many people do, myself included, is copy an application’s preferences file—either from one Mac to another (as a quick way of getting an app configured to my liking) or to replace a damaged/lost preferences file using a Time Machine backup. Until recently, this process was really simple: quit the app in question, trash the existing prefs file, insert the new prefs file, launch app.
Enter OS X 10.9, aka Mavericks, aka “the easy prefs copy killer.” Apple has made changes to the way the preferences system works in Mavericks, and one casualty of those changes is the easy replacement of an application’s preferences file. A brief bit of before-and-after, and then we’ll get to the fix—or just click the Read More link to jump right to the fix.
In prior versions of OS X, preferences files were always read by the application at launch. So as long as the app wasn’t running, if you replaced its preference file, it would read the new file the next time you launched the program.
In Mavericks, preferences are managed by a background daemon, cfprefsd. This service reads the preferences file once, when you first run the app. It then (I believe) receives notifications if you change the program’s settings while the program is running, and then writes them to the actual preferences file at certain points in time. But cfprefsd always has a copy of those settings in its cache, and that’s what the app gets when it checks its settings. (This reduces hard disk access, which is important in conserving battery life in laptops.)
Here’s the important bit: After you’ve launched an app once, it seems that any subsequent launches also get their preferences from cfprefsd. So if you try the old “replace the prefs while the app isn’t running” trick, you’ll be quite surprised to find that your program launches with its previous settings. It will do this even if you simply delete (via Finder) the old prefs file!
So how do you get around this aggressive caching of preference files?
I’m aware of three solutions, though there may be others (please comment, if you know of a better way).
Method 1:
1. Quit the app
2. Open Terminal
3. Paste killall cfprefsd then press Return. This relaunches the prefs system
4. Now relaunch the app and it should read the modified prefs file
Method 2:
1. Quit the app, and make sure it is not set to run at login
2. Delete the app’s prefs file (typically in ~/Library/Preferences, for non-sandboxed applications)
3. Logout
4. Login
5. Copy the prefs file you want to use into its home
6. Launch the app
Method 3:
1. Quit the app, leaving the ‘bad’ prefs file in place.
2. Open Terminal, paste the following, and press Return: defaults delete 3. com.COMPANY_ID.APP_ID. Note that COMPANY_ID and APP_ID are taken from the name of the app’s preferences file. Using our own Moom for example, the preferences file is named com.manytricks.Moom.plist, so the command would be defaults delete com.manytricks.Moom.
3. Copy the prefs file you want to use into the ~/Library/Preferences folder.
4. Launch the app
Enter OS X 10.9, aka Mavericks, aka “the easy prefs copy killer.” Apple has made changes to the way the preferences system works in Mavericks, and one casualty of those changes is the easy replacement of an application’s preferences file. A brief bit of before-and-after, and then we’ll get to the fix—or just click the Read More link to jump right to the fix.
In prior versions of OS X, preferences files were always read by the application at launch. So as long as the app wasn’t running, if you replaced its preference file, it would read the new file the next time you launched the program.
In Mavericks, preferences are managed by a background daemon, cfprefsd. This service reads the preferences file once, when you first run the app. It then (I believe) receives notifications if you change the program’s settings while the program is running, and then writes them to the actual preferences file at certain points in time. But cfprefsd always has a copy of those settings in its cache, and that’s what the app gets when it checks its settings. (This reduces hard disk access, which is important in conserving battery life in laptops.)
Here’s the important bit: After you’ve launched an app once, it seems that any subsequent launches also get their preferences from cfprefsd. So if you try the old “replace the prefs while the app isn’t running” trick, you’ll be quite surprised to find that your program launches with its previous settings. It will do this even if you simply delete (via Finder) the old prefs file!
So how do you get around this aggressive caching of preference files?
I’m aware of three solutions, though there may be others (please comment, if you know of a better way).
Method 1:
1. Quit the app
2. Open Terminal
3. Paste killall cfprefsd then press Return. This relaunches the prefs system
4. Now relaunch the app and it should read the modified prefs file
Method 2:
1. Quit the app, and make sure it is not set to run at login
2. Delete the app’s prefs file (typically in ~/Library/Preferences, for non-sandboxed applications)
3. Logout
4. Login
5. Copy the prefs file you want to use into its home
6. Launch the app
Method 3:
1. Quit the app, leaving the ‘bad’ prefs file in place.
2. Open Terminal, paste the following, and press Return: defaults delete 3. com.COMPANY_ID.APP_ID. Note that COMPANY_ID and APP_ID are taken from the name of the app’s preferences file. Using our own Moom for example, the preferences file is named com.manytricks.Moom.plist, so the command would be defaults delete com.manytricks.Moom.
3. Copy the prefs file you want to use into the ~/Library/Preferences folder.
4. Launch the app
IT Security: Google and Yahoo Malaysia Hijacked
Google.com.my and Yahoo.com.my is currently down for desktop users after the site was hacked and defaced by unknown culprits. The attack, which happened just about an hour ago, replaced the Google Malaysia and Yahoo Malaysia front pages with a message from the hackers.
The problem was first noticed by users who took to social media to highlight the problem. Google Tweeted that it looks like a DNS redirect. This would mean that Google was not actually hacked, but rather the domain name registry with MYNiC.
It is likely that the problem lies with MYNiC, as the message from the hackers indicates that it was done by the same group who hacked the domain name registrar two years ago. However, the scope of this hack appears to be much smaller, and only affecting the Google Malaysia and Yahoo Malaysia websites.
There are two updates from Google so far:
[Update #1] Google has tweeted that some users are still seeing the problem. We here at Lowyat.NET are also seeing the issue, although some are reporting that it can only be seen when using Google DNS. It also looks like Google Malaysia works properly on mobile devices.
[Update #2] Google has issued an official statement about the incident:
“We’re aware that some users are having trouble connecting to google.com.my, or are being directed to a different website. Google services for the google.com.my domain are not compromised. We’ve reached out to the organization responsible for managing this domain name and hope to have the issue resolved.” It also looks like the Google Malaysia Adwords site was also a victim of the attack. We do not know why this was made a target, but it looks like collateral damage from the hackers.
However, for Yahoo Malaysia, the homepage is currently still down. There is no statement from Yahoo so far.
Friday, 10 April 2015
Microsoft: SQL Performance Benchmark
1. Batch Requests/Sec
Batch Requests/Sec measures the number of batches SQL Server is receiving per second. This counter is a good indicator of how much activity is being processed by your SQL Server box. The higher the number, the more queries are being executed on your box. Like many counters, there is no single number that can be used universally to indicate your machine is too busy. Today’s machines are getting more and more powerful all the time and therefore can process more batch requests per second. You should review this counter over time to determine a baseline number for your environment.
2. SQL Compilations/Sec
The SQL Compilations/Sec measure the number of times SQL Server compiles an execution plan per second. Compiling an execution plan is a resource-intensive operation. Compilations/Sec should be compared with the number of Batch Requests/Sec to get an indication of whether or not complications might be hurting your performance. To do that, divide the number of batch requests by the number of compiles per second to give you a ratio of the number of batches executed per compile. Ideally you want to have one compile per every 10 batch requests.
3. SQL Re-Compilations/Sec
When the execution plan is invalidated due to some significant event, SQL Server will re-compile it. The Re-compilations/Sec counter measures the number of time a re-compile event was triggered per second. Re-compiles, like compiles, are expensive operations so you want to minimize the number of re-compiles. Ideally you want to keep this counter less than 10% of the number of Compilations/Sec.
Batch Requests/Sec measures the number of batches SQL Server is receiving per second. This counter is a good indicator of how much activity is being processed by your SQL Server box. The higher the number, the more queries are being executed on your box. Like many counters, there is no single number that can be used universally to indicate your machine is too busy. Today’s machines are getting more and more powerful all the time and therefore can process more batch requests per second. You should review this counter over time to determine a baseline number for your environment.
2. SQL Compilations/Sec
The SQL Compilations/Sec measure the number of times SQL Server compiles an execution plan per second. Compiling an execution plan is a resource-intensive operation. Compilations/Sec should be compared with the number of Batch Requests/Sec to get an indication of whether or not complications might be hurting your performance. To do that, divide the number of batch requests by the number of compiles per second to give you a ratio of the number of batches executed per compile. Ideally you want to have one compile per every 10 batch requests.
3. SQL Re-Compilations/Sec
When the execution plan is invalidated due to some significant event, SQL Server will re-compile it. The Re-compilations/Sec counter measures the number of time a re-compile event was triggered per second. Re-compiles, like compiles, are expensive operations so you want to minimize the number of re-compiles. Ideally you want to keep this counter less than 10% of the number of Compilations/Sec.
Wednesday, 8 April 2015
PRTG: Cloud Ping Sensor
The sensor can show the response times of the target server pinged from the following locations:
- Asia Pacific: Singapore
- Asia Pacific: Sydney
- Asia Pacific: Tokyo
- EU Central: Frankfurt
- EU West: Ireland
- South America: Sao Paulo
- US East: Northern Virginia
- US West: Northern California
- US West: Oregon
- Global average response time
Tuesday, 7 April 2015
IT Technology: Dell DPACK 1.5.5 Dell DPACK Collector
Dell DPACK 1.5.5 Dell DPACK collector is a small executable file that runs for approximately 24 hours during which time it measures disk activity and memory/CPU utilization for each server. The output of the data collector is an iokit file that can be returned to the sales team via email. The data analyzer organizes the collected data into a detailed, customer-ready report that the sales team can use to recommend hardware modifications and/or investments to improve storage solution performance. The data collector can support multiple platforms such as Windows, VMware, Linux, Solaris and Unix.
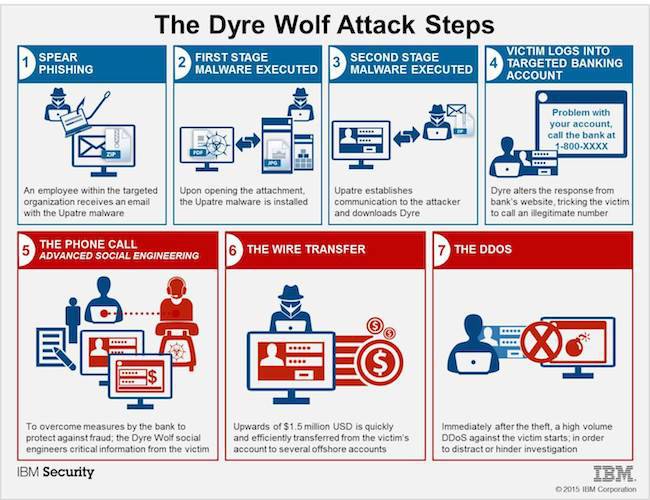
IT Security: "Dyre Wolf" Attacks Target Enterprise Bank Accounts by IBM
A combination of new malware and old-fashioned social engineering has been used to rob companies of more than US$1 million, according to a new study from IBM.
The attacks, dubbed “Dyre Wolf” by IBM, suggests the work of experienced online criminals brazenly attempting to rip off large organizations.
“As we continue to see, cybercriminals grow in resourcefulness and productivity at alarming rates. They are sharing expertise on a global scale via the deep Web and launching carefully planned, long-term attacks to attain the highest return on investment,” wrote John Kuhn, IBM senior threat researcher, in a blog post co-authored with fellow IBM researcher Lance Mueller.
Dyre Wolf uses a variant of Dyre, which is malware written to target the websites of hundreds of banks..
“Since its start in 2014, Dyre has evolved to become simultaneously sophisticated and easy to use, enabling cybercriminals to go for the bigger payout,” Kuhn wrote. An organized but as-of-yet unidentified group of attackers also rely on talking to users by phone, in order to bypass the two-factor authentication most organizations have put in place to thwart online attacks
Since October, IBM has seen a spike in the infection rate of Dyre on corporate networks, spiking from 500 instances to nearly 3,500. It estimates that anywhere from $500,000 to $1.5 million has been lost through Dyre-based attacks
IBM posted a paper outlining in detail how the attack works.
A user is tricked into installing the Dyer software on the machine by the usual means, perhaps by clicking on a malicious email attachment.
The installed program remains silent until a user attempts to log onto a bank website recognized by Dyre. At that point, a Web page will pop up explaining the site is experiencing technical difficulties and that the user should call the help center to gain access.
The attackers are sophisticated enough to rig the software so that when the user calls, the attackers answer the phone posing as a representative from the bank. They then trick the user into giving up the password. By the time the phone call is finished, money is already transferred out of the enterprise’s account and is rapidly moving across different banks around the globe to evade detection.
IBM has estimated that 95 percent of all corporate attacks rely on some form of human error.
Most employees have already been trained not to click on unknown documents received by email, as well as to not give up passwords over the phone. A single inattentive user, however, could result in the loss of large sums of money.
To guard against Dyre Wolf, security professionals should reinforce company best practices that should already be in place. Employees should be reminded that banks never ask for passwords and that they should report any suspicious behavior. An organization may also wish to carry out mock-attacks to ensure that employees are fully trained on how to handle such incidents, Kuhn said.
Thursday, 2 April 2015
IT Security: Personal Details of World Leaders Accidentally Revealed by G20 Organisers
The personal details of world leaders at the last G20 summit were accidentally disclosed by the Australian immigration department, which did not consider it necessary to inform those world leaders of the privacy breach.
The Guardian can reveal an employee of the agency inadvertently sent the passport numbers, visa details and other personal identifiers of all world leaders attending the summit to the organisers of the Asian Cup football tournament.
The United States president, Barack Obama, the Russian president, Vladimir Putin, the German chancellor, Angela Merkel, the Chinese president, Xi Jinping, the Indian prime minister, Narendra Modi, the Japanese prime minister, Shinzo Abe, the Indonesian president, Joko Widodo, and the British prime minister, David Cameron, were among those who attended the Brisbane summit in November and whose details were exposed.
The Australian privacy commissioner was contacted by the director of the visa services division of Australia’s Department of Immigration and Border Protection to inform them of the data breach on 7 November 2014 and seek urgent advice.
In an email sent to the commissioner’s office, obtained under Australia’s freedom of information laws, the breach is attributed to an employee who mistakenly emailed a member of the local organising committee of the Asian Cup – held in Australia in January – with the personal information.
“The personal information which has been breached is the name, date of birth, title, position nationality, passport number, visa grant number and visa subclass held relating to 31 international leaders (ie prime ministers, presidents and their equivalents) attending the G20 leaders summit,” the officer wrote.
“The cause of the breach was human error. [Redacted] failed to check that the autofill function in Microsoft Outlook had entered the correct person’s details into the email ‘To’ field. This led to the email being sent to the wrong person.
“The matter was brought to my attention directly by [redacted] immediately after receiving an email from [the recipient] informing them that they had sent the email to the wrong person.
“The risk remains only to the extent of human error, but there was nothing systemic or institutional about the breach.”
The officer wrote that it was “unlikely that the information is in the public domain”, and said the absence of other personal identifiers “limits significantly” the risk of the breach. The unauthorised recipient had deleted the email and “emptied their deleted items folder”.
“The Asian Cup local organising committee do not believe the email to be accessible, recoverable or stored anywhere else in their systems,” the letter said.
The immigration officer then recommended that the world leaders not be made aware of the breach of their personal information.
“Given that the risks of the breach are considered very low and the actions that have been taken to limit the further distribution of the email, I do not consider it necessary to notify the clients of the breach,” she wrote.
The recommendation not to disclose the breach to the world leaders may be at odds with privacy law in some of their countries.
Britain, Germany and France all have different forms of mandatory data breach notification laws that require individuals affected by data breaches to be informed.
It is not clear whether the immigration department subsequently notified the world leaders of the breach after the initial assessment.
The office of the Australian immigration minister, Peter Dutton, did not respond to questions.
Australia’s deputy opposition leader, Tanya Plibersek, called on Tony Abbott to explain why the world leaders were not notified of the breach.
“The prime minister and the immigration minister must explain this serious incident and the decision not to inform those affected,” she said.
Disclosure of the data breach is likely to embarrass the Australian government after controversial mandatory data retention laws were passed last week.
The passage of the laws – which require telecommunications companies to store certain types of phone and web data for two years – has been marked by concerns about the adequacy of privacy safeguards by companies and government agencies that will handle the data.
The Greens senator Sarah Hanson-Young said: “Only last week the government was calling on the Australian people to trust them with their online data, and now we find out they have disclosed the details of our world leaders.
“This is another serious gaffe by an incompetent government.”
Australia’s immigration department was also responsible for the country’s largest ever data breach by a government agency.
In February 2014 the Guardian revealed the agency had inadvertently disclosed the personal details of almost 10,000 people in detention – many of whom were asylum seekers – in a public file on its website.
The Guardian can reveal an employee of the agency inadvertently sent the passport numbers, visa details and other personal identifiers of all world leaders attending the summit to the organisers of the Asian Cup football tournament.
The United States president, Barack Obama, the Russian president, Vladimir Putin, the German chancellor, Angela Merkel, the Chinese president, Xi Jinping, the Indian prime minister, Narendra Modi, the Japanese prime minister, Shinzo Abe, the Indonesian president, Joko Widodo, and the British prime minister, David Cameron, were among those who attended the Brisbane summit in November and whose details were exposed.
The Australian privacy commissioner was contacted by the director of the visa services division of Australia’s Department of Immigration and Border Protection to inform them of the data breach on 7 November 2014 and seek urgent advice.
In an email sent to the commissioner’s office, obtained under Australia’s freedom of information laws, the breach is attributed to an employee who mistakenly emailed a member of the local organising committee of the Asian Cup – held in Australia in January – with the personal information.
“The personal information which has been breached is the name, date of birth, title, position nationality, passport number, visa grant number and visa subclass held relating to 31 international leaders (ie prime ministers, presidents and their equivalents) attending the G20 leaders summit,” the officer wrote.
“The cause of the breach was human error. [Redacted] failed to check that the autofill function in Microsoft Outlook had entered the correct person’s details into the email ‘To’ field. This led to the email being sent to the wrong person.
“The matter was brought to my attention directly by [redacted] immediately after receiving an email from [the recipient] informing them that they had sent the email to the wrong person.
“The risk remains only to the extent of human error, but there was nothing systemic or institutional about the breach.”
The officer wrote that it was “unlikely that the information is in the public domain”, and said the absence of other personal identifiers “limits significantly” the risk of the breach. The unauthorised recipient had deleted the email and “emptied their deleted items folder”.
“The Asian Cup local organising committee do not believe the email to be accessible, recoverable or stored anywhere else in their systems,” the letter said.
The immigration officer then recommended that the world leaders not be made aware of the breach of their personal information.
“Given that the risks of the breach are considered very low and the actions that have been taken to limit the further distribution of the email, I do not consider it necessary to notify the clients of the breach,” she wrote.
The recommendation not to disclose the breach to the world leaders may be at odds with privacy law in some of their countries.
Britain, Germany and France all have different forms of mandatory data breach notification laws that require individuals affected by data breaches to be informed.
It is not clear whether the immigration department subsequently notified the world leaders of the breach after the initial assessment.
The office of the Australian immigration minister, Peter Dutton, did not respond to questions.
Australia’s deputy opposition leader, Tanya Plibersek, called on Tony Abbott to explain why the world leaders were not notified of the breach.
“The prime minister and the immigration minister must explain this serious incident and the decision not to inform those affected,” she said.
Disclosure of the data breach is likely to embarrass the Australian government after controversial mandatory data retention laws were passed last week.
The passage of the laws – which require telecommunications companies to store certain types of phone and web data for two years – has been marked by concerns about the adequacy of privacy safeguards by companies and government agencies that will handle the data.
The Greens senator Sarah Hanson-Young said: “Only last week the government was calling on the Australian people to trust them with their online data, and now we find out they have disclosed the details of our world leaders.
“This is another serious gaffe by an incompetent government.”
Australia’s immigration department was also responsible for the country’s largest ever data breach by a government agency.
In February 2014 the Guardian revealed the agency had inadvertently disclosed the personal details of almost 10,000 people in detention – many of whom were asylum seekers – in a public file on its website.
Wednesday, 1 April 2015
Microsoft: Exchange Report based on Display Name, Account Status, Memberof and Hide from Exchange Address Lists
The following Powershell script allows you to generate an Exchange report based on the display name, account status, memberof and hide from Exchange address lists:
param(
[Parameter(ParameterSetName='file')] [string]$file,
[Parameter(ParameterSetName='server')] [string]$server,
[Parameter(ParameterSetName='mailbox')] [string]$mailbox,
[Parameter(ParameterSetName='all')] [switch]$all,
[string]$filename
)
$ErrorActionPreference = "SilentlyContinue"
$WarningPreference = "SilentlyContinue"
$report = @()
#Set recipient scope
$2007snapin = Get-PSSnapin -Name Microsoft.Exchange.Management.PowerShell.Admin
if ($2007snapin)
{
$AdminSessionADSettings.ViewEntireForest = 1
}
else
{
$2010snapin = Get-PSSnapin -Name Microsoft.Exchange.Management.PowerShell.E2010
if ($2010snapin)
{
Set-ADServerSettings -ViewEntireForest $true
}
}
#If no filename specified, generate report file name with random strings for uniqueness
if ($filename)
{
$reportfile = $filename
}
else
{
$timestamp = Get-Date -UFormat %Y%m%d-%H%M
$random = -join(48..57+65..90+97..122 | ForEach-Object {[char]$_} | Get-Random -Count 6)
$reportfile = "MailboxReport-$timestamp-$random.csv"
}
#Add dependencies
Import-Module ActiveDirectory
#Get the mailbox list
Write-Host -ForegroundColor White "Collecting mailbox list"
if($all) { $mailboxes = @(Get-Mailbox -resultsize unlimited -IgnoreDefaultScope) }
if($server) { $mailboxes = @(Get-Mailbox -server $server -resultsize unlimited -IgnoreDefaultScope) }
if($hidden){ $mailboxes = @(Get-Mailbox -hiddenfromaddresslistsenabled $hidden -resultsize unlimited -IgnoreDefaultScope) }
if($file) { $mailboxes = @(Get-Content $file | Get-Mailbox -resultsize unlimited) }
if($mailbox) { $mailboxes = @(Get-Mailbox $mailbox) }
#Get the report
Write-Host -ForegroundColor White "Collecting report data"
$mailboxcount = $mailboxes.count
$i = 0
#Loop through mailbox list and find the aged mailboxes
foreach ($mb in $mailboxes)
{
$i = $i + 1
$pct = $i/$mailboxcount * 100
Write-Progress -Activity "Collecting mailbox details" -Status "Processing mailbox $i of $mailboxcount - $mb" -PercentComplete $pct
$user = Get-User $mb
$aduser = Get-ADUser $mb.samaccountname -Properties Enabled,AccountExpirationDate
$aduserr = Get-ADUser $mb.samaccountname -Properties *
$member = ($aduserr.memberof | % { (Get-ADGroup $_).Name; }) -join ';'
#Create a custom PS object to aggregate the data we're interested in
$userObj = New-Object PSObject
$userObj | Add-Member NoteProperty -Name "DisplayName" -Value $mb.DisplayName
$userObj | Add-Member NoteProperty -Name "Enabled" -Value $aduser.Enabled
$userObj | Add-Member NoteProperty -Name "MemberOf" -Value $member
$userObj | Add-Member NoteProperty -Name "Hide from Exchange" -Value $mb.HiddenFromAddressListsEnabled
#Add the object to the report
$report = $report += $userObj
}
#Catch zero item results
$reportcount = $report.count
if ($reportcount -eq 0)
{
Write-Host -ForegroundColor Yellow "No mailboxes were found matching that criteria."
}
else
{
#Output single mailbox report to console, otherwise output to CSV file
if ($mailbox)
{
$report | Format-List
}
else
{
$report | Export-Csv -Path $reportfile -NoTypeInformation
Write-Host -ForegroundColor White "Report written to $reportfile in current path."
Get-Item $reportfile
}
}
param(
[Parameter(ParameterSetName='file')] [string]$file,
[Parameter(ParameterSetName='server')] [string]$server,
[Parameter(ParameterSetName='mailbox')] [string]$mailbox,
[Parameter(ParameterSetName='all')] [switch]$all,
[string]$filename
)
$ErrorActionPreference = "SilentlyContinue"
$WarningPreference = "SilentlyContinue"
$report = @()
#Set recipient scope
$2007snapin = Get-PSSnapin -Name Microsoft.Exchange.Management.PowerShell.Admin
if ($2007snapin)
{
$AdminSessionADSettings.ViewEntireForest = 1
}
else
{
$2010snapin = Get-PSSnapin -Name Microsoft.Exchange.Management.PowerShell.E2010
if ($2010snapin)
{
Set-ADServerSettings -ViewEntireForest $true
}
}
#If no filename specified, generate report file name with random strings for uniqueness
if ($filename)
{
$reportfile = $filename
}
else
{
$timestamp = Get-Date -UFormat %Y%m%d-%H%M
$random = -join(48..57+65..90+97..122 | ForEach-Object {[char]$_} | Get-Random -Count 6)
$reportfile = "MailboxReport-$timestamp-$random.csv"
}
#Add dependencies
Import-Module ActiveDirectory
#Get the mailbox list
Write-Host -ForegroundColor White "Collecting mailbox list"
if($all) { $mailboxes = @(Get-Mailbox -resultsize unlimited -IgnoreDefaultScope) }
if($server) { $mailboxes = @(Get-Mailbox -server $server -resultsize unlimited -IgnoreDefaultScope) }
if($hidden){ $mailboxes = @(Get-Mailbox -hiddenfromaddresslistsenabled $hidden -resultsize unlimited -IgnoreDefaultScope) }
if($file) { $mailboxes = @(Get-Content $file | Get-Mailbox -resultsize unlimited) }
if($mailbox) { $mailboxes = @(Get-Mailbox $mailbox) }
#Get the report
Write-Host -ForegroundColor White "Collecting report data"
$mailboxcount = $mailboxes.count
$i = 0
#Loop through mailbox list and find the aged mailboxes
foreach ($mb in $mailboxes)
{
$i = $i + 1
$pct = $i/$mailboxcount * 100
Write-Progress -Activity "Collecting mailbox details" -Status "Processing mailbox $i of $mailboxcount - $mb" -PercentComplete $pct
$user = Get-User $mb
$aduser = Get-ADUser $mb.samaccountname -Properties Enabled,AccountExpirationDate
$aduserr = Get-ADUser $mb.samaccountname -Properties *
$member = ($aduserr.memberof | % { (Get-ADGroup $_).Name; }) -join ';'
#Create a custom PS object to aggregate the data we're interested in
$userObj = New-Object PSObject
$userObj | Add-Member NoteProperty -Name "DisplayName" -Value $mb.DisplayName
$userObj | Add-Member NoteProperty -Name "Enabled" -Value $aduser.Enabled
$userObj | Add-Member NoteProperty -Name "MemberOf" -Value $member
$userObj | Add-Member NoteProperty -Name "Hide from Exchange" -Value $mb.HiddenFromAddressListsEnabled
#Add the object to the report
$report = $report += $userObj
}
#Catch zero item results
$reportcount = $report.count
if ($reportcount -eq 0)
{
Write-Host -ForegroundColor Yellow "No mailboxes were found matching that criteria."
}
else
{
#Output single mailbox report to console, otherwise output to CSV file
if ($mailbox)
{
$report | Format-List
}
else
{
$report | Export-Csv -Path $reportfile -NoTypeInformation
Write-Host -ForegroundColor White "Report written to $reportfile in current path."
Get-Item $reportfile
}
}
Google: Google Spreadsheet Email Alert based on the Input Data
The Google script below allows you to automate the Google Spreadsheet to send an email alert based on the input data:
function checkReminder() {
// get the spreadsheet object
var spreadsheet = SpreadsheetApp.getActiveSpreadsheet();
// set the first sheet as active
SpreadsheetApp.setActiveSheet(spreadsheet.getSheets()[0]);
// fetch this sheet
var sheet = spreadsheet.getActiveSheet();
// figure out what the last row is
var lastRow = sheet.getLastRow();
// start with row 10
var startRow = 10;
// grab column 3 (the 'days left' column)
var range = sheet.getRange(10,3,lastRow-startRow+1,1 );
var numRows = range.getNumRows();
var days_left_values = range.getValues();
// grab the description column
range = sheet.getRange(10, 6, lastRow-startRow+1, 1);
var reminder_info_values = range.getValues();
// grab the vendor column
range = sheet.getRange(10, 5, lastRow-startRow+1, 1);
var reminder_vendor_values = range.getValues();
var warning_count = 0;
var msg = "";
// Loop over the days left values
for (var i = 0; i <= numRows - 1; i++) {
var days_left = days_left_values[i][0];
if(days_left == 90) {
// if it's exactly 90, do something with the data.
var vendor = reminder_vendor_values[i][0];
var description = reminder_info_values[i][0];
msg = msg + "Reminder: "+vendor+" "+description+" is due in "+days_left+" days.\n";
warning_count++;
}
}
if(warning_count) {
MailApp.sendEmail("italert@marlboroughcollege.my",
"Contract and Agreement Reminder", msg);
}
}
function checkReminder() {
// get the spreadsheet object
var spreadsheet = SpreadsheetApp.getActiveSpreadsheet();
// set the first sheet as active
SpreadsheetApp.setActiveSheet(spreadsheet.getSheets()[0]);
// fetch this sheet
var sheet = spreadsheet.getActiveSheet();
// figure out what the last row is
var lastRow = sheet.getLastRow();
// start with row 10
var startRow = 10;
// grab column 3 (the 'days left' column)
var range = sheet.getRange(10,3,lastRow-startRow+1,1 );
var numRows = range.getNumRows();
var days_left_values = range.getValues();
// grab the description column
range = sheet.getRange(10, 6, lastRow-startRow+1, 1);
var reminder_info_values = range.getValues();
// grab the vendor column
range = sheet.getRange(10, 5, lastRow-startRow+1, 1);
var reminder_vendor_values = range.getValues();
var warning_count = 0;
var msg = "";
// Loop over the days left values
for (var i = 0; i <= numRows - 1; i++) {
var days_left = days_left_values[i][0];
if(days_left == 90) {
// if it's exactly 90, do something with the data.
var vendor = reminder_vendor_values[i][0];
var description = reminder_info_values[i][0];
msg = msg + "Reminder: "+vendor+" "+description+" is due in "+days_left+" days.\n";
warning_count++;
}
}
if(warning_count) {
MailApp.sendEmail("italert@marlboroughcollege.my",
"Contract and Agreement Reminder", msg);
}
}
Google: Pac-Man in Google Maps
Ever imagine what it'd be like to play a monster game of Pac-Man through the streets of your hometown? Now you can, sort of, as Google has built a fully playable game of Pac-Man into Google Maps.
To play the game, simply go to Google Maps in a browser on your computer, or on the updated iOS and Android Google Maps apps, and find a location near you with a good amount of streets.
From there, click the Pac-Man button in the bottom left corner, and Google will transform those streets into a playable version of Pac-Man. The controls are pretty simple: just tap on the up, down, left and right arrows to move Pac-Man around while you collect dots and cherries, all while avoiding being killed by ghosts.
April Fools' is Wednesday, meaning you'll see some pretty bizarre things. If this is Google's idea of an April Fools' stunt, it's pretty amazing. If you, like me, were totally jealous of that guy who got to play Pac-Man for real in the Bud Light Super Bowl Ad, playing Pac-Man in your town of choice on Google Maps might just be the next best thing.
Subscribe to:
Comments (Atom)